How to Use a Crypto Wallet Safely takes center stage, this opening passage beckons readers with american high school hip style into a world crafted with good knowledge, ensuring a reading experience that is both absorbing and distinctly original.
When it comes to navigating the world of digital assets, ensuring the safety of your crypto wallet is key. Let’s dive into the essentials of keeping your funds secure in the digital realm.
Importance of Crypto Wallet Security: How To Use A Crypto Wallet Safely
In the fast-paced digital asset world, ensuring the security of your crypto wallet is of paramount importance. With the rise of cryptocurrencies and the increasing value they hold, protecting your assets from theft, hacks, and scams is crucial to safeguarding your investments.
Risks of Using an Insecure Wallet
- An insecure crypto wallet is susceptible to hacking attempts by cybercriminals looking to steal your funds.
- Phishing attacks can trick users into revealing their private keys or sensitive information, leading to unauthorized access to their wallets.
- If you store your cryptocurrencies on an insecure wallet, you risk losing all your funds in case of a security breach or a compromised platform.
Consequences of Using an Unsafe Crypto Wallet
- Loss of funds: Hackers can drain your wallet of all its contents, leaving you with no way to recover your stolen cryptocurrencies.
- Identity theft: Insecure wallets can expose your personal information, making you vulnerable to identity theft and other fraudulent activities.
- Damaged reputation: Falling victim to a crypto wallet hack can tarnish your reputation in the digital asset community and lead to mistrust from other users.
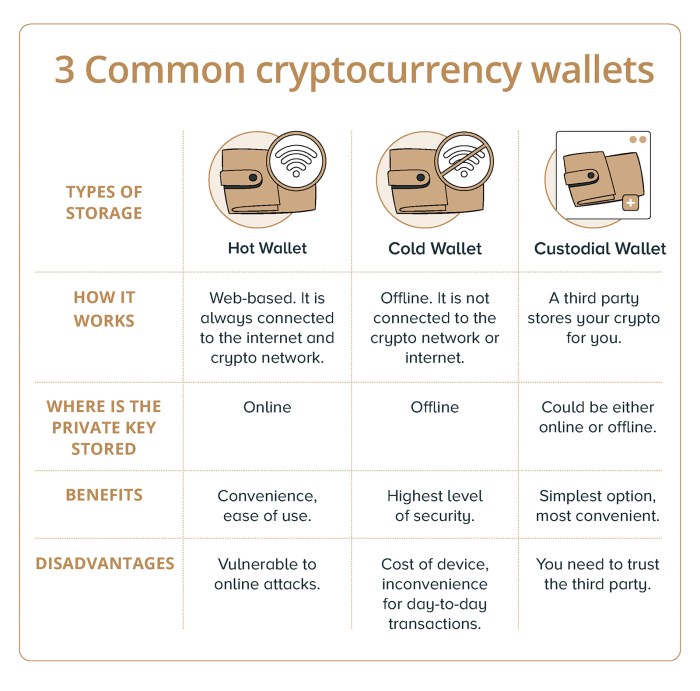
Types of Crypto Wallets
When it comes to storing your cryptocurrency, there are different types of wallets available for users to choose from. These wallets vary in terms of security measures and accessibility, catering to the diverse needs of crypto holders.
Hot Wallets
Hot wallets, also known as online wallets, are connected to the internet and are easily accessible for transactions. They are convenient for frequent trading or spending of cryptocurrencies. However, due to their online nature, hot wallets are more susceptible to hacking and cyber attacks, making them less secure compared to cold wallets.
Cold Wallets
Cold wallets, on the other hand, are offline wallets that store your cryptocurrency keys in an offline environment, away from potential cyber threats. Examples of cold wallets include hardware wallets and paper wallets. While cold wallets provide a higher level of security for long-term storage of cryptocurrency, they may not be as convenient for regular transactions as hot wallets.
Overall, the choice between hot wallets and cold wallets depends on your individual needs and preferences. It’s essential to weigh the pros and cons of each type of wallet to ensure the safety of your crypto assets.
Setting Up a Secure Crypto Wallet
When setting up a crypto wallet, it is crucial to prioritize security measures to protect your digital assets from potential threats. Here is a step-by-step guide on how to set up a secure crypto wallet:
Strong Password and Two-Factor Authentication
- Create a strong and unique password that combines letters, numbers, and special characters.
- Enable two-factor authentication (2FA) to add an extra layer of security to your wallet.
- Use reputable 2FA apps like Google Authenticator or Authy for added protection.
Additional Security Measures, How to Use a Crypto Wallet Safely
- Consider using biometric authentication, such as fingerprint or facial recognition, if supported by your wallet.
- Utilize hardware keys like Ledger Nano S or Trezor for offline storage of your private keys.
- Regularly update your wallet software to ensure you have the latest security patches and features.
Safe Practices for Using a Crypto Wallet

When it comes to using a crypto wallet, it’s crucial to follow safe practices to protect your assets and information. Here are some tips to help you navigate the crypto space securely.
Safely Sending and Receiving Cryptocurrency
- Always double-check the recipient’s wallet address before sending any cryptocurrency to avoid sending funds to the wrong address.
- Consider using a QR code to scan the recipient’s wallet address instead of manually typing it to minimize the risk of human error.
- Avoid sharing your private keys or recovery phrases with anyone to prevent unauthorized access to your wallet.
Importance of Regularly Updating Wallet Software
Regularly updating your wallet software is essential to patch any vulnerabilities and ensure your wallet’s security features are up to date.
Safely Storing Backup and Recovery Phrases
- Keep your backup and recovery phrases in a secure and offline location, such as a safe deposit box or a hardware wallet, to prevent unauthorized access.
- Avoid storing your backup phrases on electronic devices or cloud storage, as they are more susceptible to hacking and data breaches.
- Consider using a passphrase or additional security measures to encrypt your backup phrases for an added layer of protection.
Recognizing Common Scams and Risks

Cryptocurrency users need to be aware of common scams and risks that can compromise the security of their crypto wallets. By understanding these threats, users can take steps to protect their digital assets.
Common Scams Targeting Crypto Wallet Users
- Phishing Scams: Scammers often use emails, messages, or websites that appear legitimate to trick users into revealing their private keys or passwords. Always double-check the sender’s email address and avoid clicking on suspicious links.
- Ponzi Schemes: Some scammers promise high returns on investments but actually use new investors’ funds to pay existing investors. Be cautious of any investment opportunities that seem too good to be true.
- Impersonation Scams: Scammers may impersonate famous personalities or crypto influencers to deceive users into sending them cryptocurrency. Verify the identity of anyone requesting crypto transactions.
Avoiding Phishing Attacks
- Double-Check URLs: Before entering any sensitive information, ensure that the website URL is correct and secure (https://).
- Enable Two-Factor Authentication: Adding an extra layer of security can prevent unauthorized access to your crypto wallet.
- Avoid Unsecured Networks: Be cautious when accessing your wallet on public Wi-Fi networks, as they may not be secure.
Verifying Crypto Transactions
- Check Wallet Addresses: Before sending funds, verify the recipient’s wallet address to avoid sending cryptocurrency to the wrong person.
- Confirm Transaction Details: Review all transaction details, including the amount and recipient, before confirming the transaction.
- Use Reliable Sources: When in doubt, consult official sources or community forums to verify the authenticity of a crypto transaction.





